Our cutting-edge approach ensures Real-time Monitoring, Automated Incident Analysis, and Proactive Threat Hunting, providing robust protection to your Infrastructure.
Security Operation Center
Our SOC is more than a command center; it’s your shield against evolving cyber threats.
What is SOC ?
In cybersecurity, a SOC is a centralized unit that deals with security issues at both organizational and technical levels. It monitors, detects, and responds to security incidents using a variety of tools and technologies.
Protect your business 24/7 with our managed SOC services.
Our Managed Security Operations Center (SOC) services offer a proactive approach to security, providing Continuous Monitoring, Detection Analysis, and response to security incidents. Our Managed SOC leverages advanced technologies and expert security professionals to monitor your IT infrastructure, networks, endpoints, and applications 24/7, ensuring that potential threats are identified and neutralized before they can cause harm.
Advantages of our managed SOC service
In today’s world, cyber threats are rapidly evolving, making it increasingly challenging for businesses to keep up with the latest security risks. A Managed Security Operations Center (SOC) provides a comprehensive solution to address these challenges, offering round-the-clock monitoring, detection, and response capabilities.
Choose our managed SOC services for 24/7 monitoring, cutting-edge AI threat detection, and rapid response. Our expert team offers tailored solutions, with proven success record and a commitment to ensuring robust protection against evolving cyber threats.
Our deep understanding of Security Protocols, combined with hands-on experience in handling complex incidents, ensures a proactive and efficient defense against potential breaches.
Our customized solutions, tailored strategies and tools to specific risks and operational requirements ensure optimal protection and efficiency to your Organization.
We have demonstrated consistent success in safeguarding client data and systems. This reliability is evidenced by a history of thwarting cyber attacks, minimizing downtime, and maintaining compliance with industry standards.
Through ongoing Training, Advanced Analytics, and Feedback Loops, Our SOC teams enhance their capabilities to ensure resilient and cutting-edge protection.
Key features of our SOC service
24/7 Active Monitoring
Experience the agility of automated CI/CD pipelines, enabling swift and reliable code deployment. Our experts design, implement, and optimize pipelines tailored to your development workflow.
Incidence Response & Management
Swift and decisive action in the event of a security incident. Minimization of damage through timely response and containment strategies.
Threat Haunting
Integration of the latest threat intelligence to stay ahead of emerging cyber threats. Continuous refinement of security measures based on real-time assessments.
Vulnerability Management
Regular assessment and identification of vulnerabilities in your infrastructure. Proactive measures to patch, update, and fortify systems against potential exploits.
SIEM & SOAR
We leverage SIEM (Security Information & Event Management) & Security Orchestration Automation and Response (SOAR) technologies to automate routine tasks and streamline security operations, improving efficiency and effectiveness.
Forensics Analysis
In-depth forensic analysis in the aftermath of a security incident. Determination of the root cause and implementation of preventive measures.
Threat Simulation
Simulated cyber threats to assess your system’s resilience. Evaluate your team’s response to sophisticated attacks, enhancing preparedness.
Security Awareness Training
We offer security awareness training programs to educate your employees about cybersecurity best practices and help them to identify and avoid phishing attempts and social engineering attacks.
Log Management
Our team collects and analyzes logs from your security devices and applications to identify potential threats and security incidents.
We Follow
NIST Cybersecurity Framework
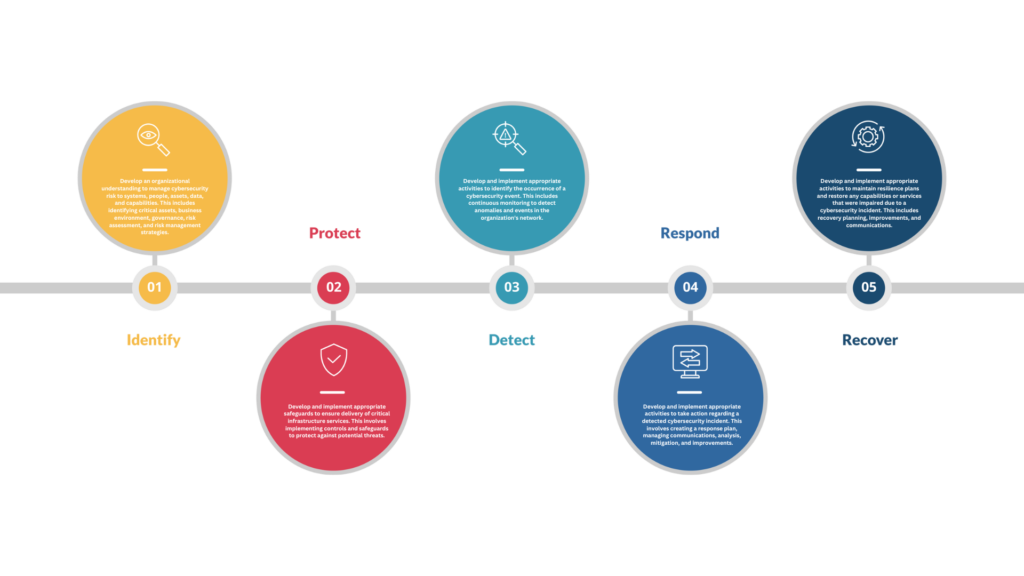
The NIST Cybersecurity Framework is a set of guidelines and best practices designed to help organizations manage and reduce cybersecurity risks. Developed by the National Institute of Standards and Technology (NIST), the framework provides a structured approach to cybersecurity that aligns with business needs and helps organizations to understand, manage, and reduce their cybersecurity risks. It is intended to be flexible, allowing organizations of all sizes, sectors, and maturity levels to adopt it in a way that fits their unique circumstances.
Our SOC services let you concentrate on what matters
Our SOC (Security Operations Center) services are designed to let you focus on your core business activities while we handle the critical task of monitoring and protecting your digital assets. With our expert team keeping a vigilant eye on your security landscape 24/7, you can concentrate on what truly matters—driving growth and innovation for your organization.
We tailor our SOC services to your needs, continuously monitoring and securing your network with real-time threat detection. Regular updates keep you informed, so you can focus on what matters most.
Establish clear accountability for cloud spending through advanced tools and reporting dashboards that track usage and costs at both team and individual levels
Our SOC services include detailed, regular reports on your security status and incident responses. These comprehensive insights help you stay informed about your security posture and make informed decisions to enhance your overall strategy.
Why choose our SOC service
-
Proactive Defense
Anticipate and neutralize threats before they impact your business. Continuous monitoring ensures a proactive stance against evolving cyber threats.
-
Customized Solutions
Tailored security strategies based on your unique business needs and risk profile. Scalable solutions that grow with your business.
-
Business Continuity
Minimize disruptions and ensure the continuity of your business operations. Rapid response and recovery strategies to mitigate the impact of security incidents.
-
Expert Team
A team of cybersecurity experts with extensive experience in threat detection and incident response. Continuous training to stay ahead of the latest cybersecurity technologies.
-
Compliance Assurance
We prioritize the highest standards in information security management, ensuring full compliance with industry regulations and evolving standards. Safeguarding data is our core mission, so you can trust we stay ahead of the curve.
-
Client-Centric Approach
Tailoring our SOC services to meet your specific needs and challenges. Responsive and collaborative, ensuring that your unique security requirements are met with precision.
SOC Tools










Value Proposition Empowering Your Security Journey
Are you caught up in a constant struggle to manage IT challenges instead of concentrating on your core business goals?
If your technology isn’t empowering your team, but rather draining your resources, our DevOps services can steer you back in the right direction. As a dedicated DevOps solutions provider, we offer you the decisive edge to:
Strategic Partnership:
Proactive consultation to ensure our SOC solutions enhance your overall security posture.
Real-Time Insights:
Access to real-time insights and reports, providing a transparent view of your security landscape.
Scalable Security:
Future-proofing your cybersecurity infrastructure to stay ahead of emerging threats.
Continuous Improvement:
Continuous refinement of security measures based on ongoing analysis and industry best practices.
